Take a casual stroll in Manhattan and you can't help but notice that construction is booming. Cranes, scaffolding, and sidewalk sheds are everywhere. And this isn’t just a New York City phenomenon. Ground-up construction and renovation projects are picking up all across the country. Low interest rates and favorable building conditions are resulting in a surge in real estate & development projects.
Topics: Construction and Development
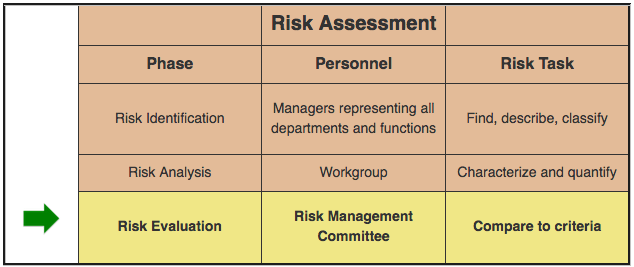
In our latest posts on Enterprise Risk management (ERM), we addressed the three phases of Risk Assessment: Risk Identification and Risk Analysis and Risk Evaluation. In this post, we turn our attention to Risk Treatment.
Topics: ERM/TCoR
Should You Pay Ransomware? No, Do These 6 Things Instead
Ransomware strikes. Your critical data files have been encrypted and your business grinds to a halt. Do you:
a) spend countless hours rebuilding from backups (if you were diligent enough to ensure they'll work) or
b) pay the perpetrator to unlock your files?
Now that ransomware is spreading like wildfire through malicious emails, "malvertising" campaigns, and exploit kits, many firms and individuals face this exact scenario.
Topics: Cyber Risk
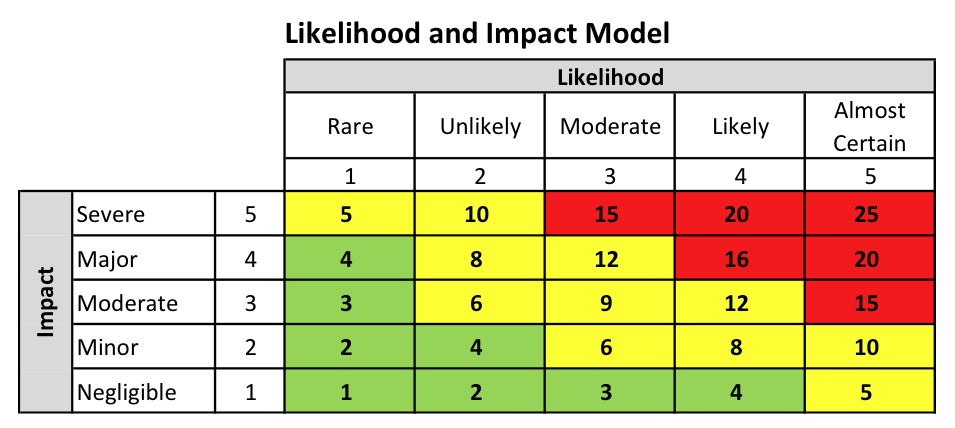
ERM | RISK ASSESSMENT PHASE THREE: RISK EVALUATION
In our two most recent posts in this series, we addressed the first two phases of Risk Assessment: Risk Identification and Risk Analysis. This post looks at the final phase, Risk Evaluation.
Topics: ERM/TCoR
4 Ways to Evaluate and Mitigate Your Company's Cyber Risk
Globalization and dependence on the internet for data storage over the past decade has exposed companies to a whole new set of risks. As this trend continues, so too does the risk associated with breaches of domestic or international servers. Massive data breaches happen with alarming frequency. In the past few years, there have been several high profile attacks affecting companies like:
Topics: Cyber Risk
Certificate of Insurance Compliance: Eliminating the Blind Spots
Errors and even outright fraud in certificates of insurance is a growing problem. We encounter a 70% noncompliance rate on initial documents.
The certificate of insurance compliance function protects a company by ensuring that its contractors have appropriate types and amounts of insurance coverage. The burden of this compliance process is often underestimated.
Topics: Compliance
Risk Analysis is the second of three phases that make up a Risk Assessment.
What are the other two phases?
Topics: ERM/TCoR
The 10 Fundamentals of a Sound Risk Management Program
More than 80% of companies don’t manage risk effectively. Is yours one of them?
A 2014 survey by a non-profit business research firm found that fewer than 20 percent of executives say their companies effectively manage risk. Companies will often have a process in place to identify and monitor risks. But they fall short when it comes to actually implementing practices to manage those risks as part of the overall strategic plan.
Topics: Risk Management
ERM | Risk Assessment Phase One: Risk Identification
Topics: ERM/TCoR
Reviewing Cyber Breach Insurance Coverage | First-Party Costs
Organizations today must regard cyber breaches not as a possibility, but as an inevitable fact of life. In this environment, it’s crucial to have a cyber liability insurance policy that adequately covers the potential loss and offers payment or reimbursement for response costs. Understanding what’s covered by the policy well before a breach occurs and building that knowledge into your company’s incident response plan is critical.
Topics: Cyber Risk